When personal and professional informational lives on one mobile device, the risk of malware attacks and huge data breaches rises. As the adoption of bring your own device policy increases, so should employee awareness when it comes to ever-growing cyber threats.
Protect your Android mobile devices
Lessons learned from the WannaCry malware
Malware infects Mac HandBrake downloads
Beware: new Mac malware on the loose

One of the defining characteristics of Apple computers is their seemingly impenetrable security system. Business and individual consumers alike who value security most in an operating system choose Apple products. Will this still be the case now that malware attacks on MacOS are increasing -- 744% in 2016, according to reports? Read on to find out.
A brief history of virtual quarantines

Malware is becoming more sophisticated every day, and we recommend several solutions for dealing with it. One of the most interesting of these is achievable via cutting-edge virtualization technology. Often referred to as sandboxing, this solution is a great way to quarantine and test suspicious applications before exposing them to your entire network.
Why you need to update Microsoft Word
Sly phishing attack catching users off guard

You pay close enough attention to the links you click to avoid clicking on something like goolge.com or evrenote.com...right? Because if you’re not, you could end up exposing your computer or smartphone to a host of malware. The newest phishing attack strategy is the worst of all, and can catch even the most astute users off guard.
Reasons to back up your mobile devices

It makes a lot of sense for electronics firms to pack a variety of functions into mobile devices and expand their usefulness. Instead of confining their use to communications, companies such as Apple, Samsung, and others have turned mobile phones into mini-computers that can serve as a substitute for your laptop, or as a storage device.
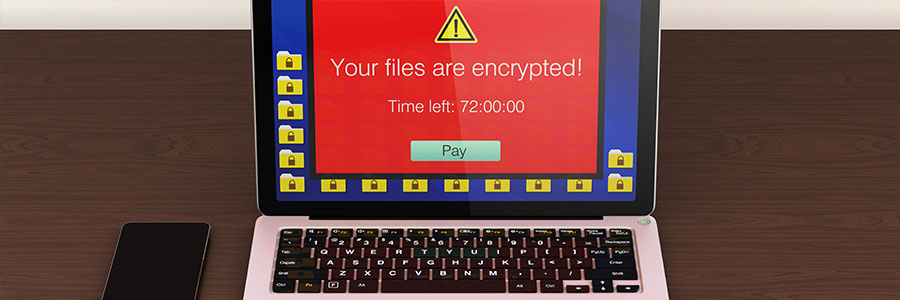
No Ransom: a place for free decryption
Why your business needs a hardware firewall

Cybersecurity is one of the final bastions of hardware superiority. More and more IT solutions are being hosted in the cloud, and business owners are being told that software is all they need to get the job done, which is half true. When it comes to perimeter security you definitely need a hardware firewall, with a little something extra.